thank you, 2021 Blog, AWS Governance, Governance360, Blog, Featured
Compliance on the Cloud is an important aspect in today’s world of remote working. As enterprises accelerate the adoption of cloud to drive frictionless business, there can be surprises on security, governance and cost without a proper framework. Relevance Lab (RL) helps enterprises speed up workload migration to the cloud with the assurance of Security, Governance and Cost Management using an integrated solution built on AWS standard products and open source framework. The key building blocks of this solution are.
Why do enterprises need Compliance as a Code?
For most enterprises, the major challenge is around governance and compliance and lack of visibility into their Cloud Infrastructure. They spend enormous time on trying to achieve compliance in a silo manner. Enterprises also spend enormous amounts of time on security and compliance with thousands of man hours. This can be addressed by automating compliance monitoring, increasing visibility across cloud with the right set of tools and frameworks. Relevance Labs Compliance as a Code framework, addresses the need of enterprises on the automation of these security & compliance. By a combination of preventive, detective and responsive controls, we help enterprises, by enforcing nearly continuous compliance and auto-remediation and there-by increase the overall security and reduce the compliance cost.
Key tools and framework of Cloud Governance 360°
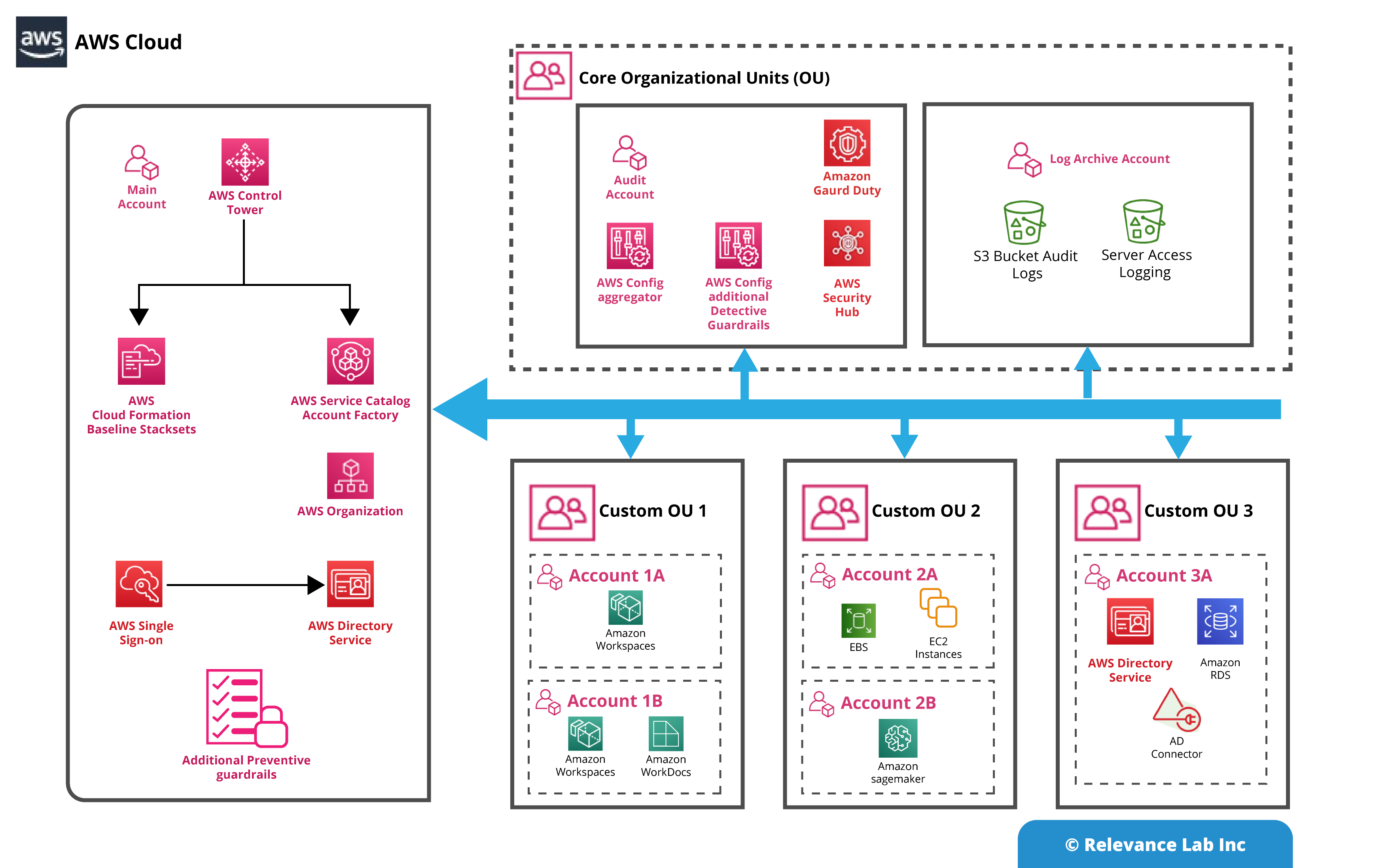
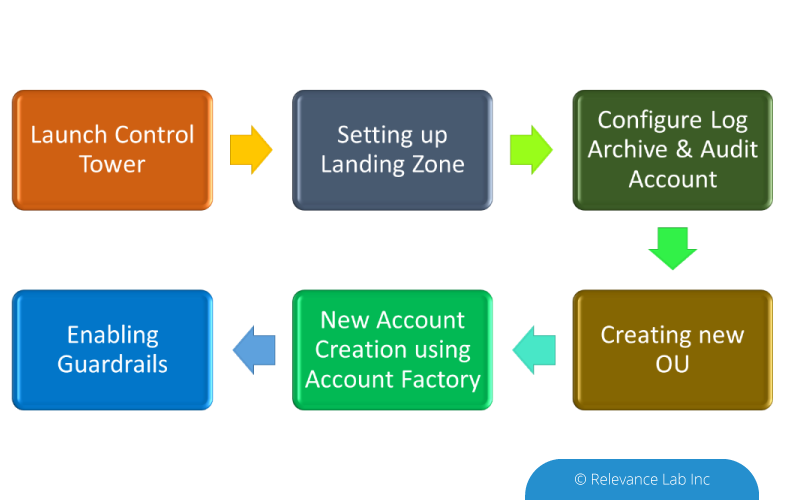
AWS Control Tower: AWS Control Tower (CT) helps Organizations set up, manage, monitor, and govern a secured multi-account using AWS best practices. Setting up a Control Tower on a new account is relatively simpler when compared to setting it up on an existing account. Once Control Tower is set up, the landing zone should have the following.
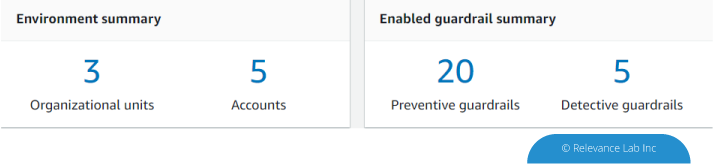
- 2 Organizational Units
- 3 accounts, a master account and isolated accounts for log archive and security audit
- 20 preventive guardrails to enforce policies
- 2 detective guardrails to detect config violations
Apart from this, you can customize the guard rails and implement them using AWS Config Rules. For more details on Control Tower implementation, refer to our earlier blog here.
Cloud Custodian: Cloud Custodian is a tool that unifies the dozens of tools and scripts most organizations use for managing their public cloud accounts into one open-source tool. It uses a stateless rules engine for policy definition and enforcement, with metrics, structured outputs and detailed reporting for Cloud Infrastructure. It integrates tightly with serverless runtimes to provide real time remediation/response with low operational overhead.
Organizations can use Custodian to manage their cloud environments by ensuring compliance to security policies, tag policies, garbage collection of unused resources, and cost management from a single tool. Custodian adheres to a Compliance as Code principle, to help you validate, dry run, and review changes to your policies. The policies are expressed in YAML and include the following.
- The type of resource to run the policy against
- Filters to narrow down the set of resources
Cloud Custodian is a rules engine for managing public cloud accounts and resources. It allows users to define policies to enable a well managed Cloud Infrastructure, that’s both secure and cost optimized. It consolidates many of the ad hoc scripts organizations have into a lightweight and flexible tool, with unified metrics and reporting.
Security Hub: AWS Security Hub gives you a comprehensive view of your security alerts and security posture across your AWS accounts. It’s a single place that aggregates, organizes, and prioritizes your security alerts, or findings, from multiple AWS services, such as Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Identity and Access Management (IAM) Access Analyzer, and AWS Firewall Manager, as well as from AWS Partner solutions like Cloud Custodian. You can also take action on these security findings by investigating them in Amazon Detective or by using Amazon CloudWatch Event rules to send the findings to an ITSM, chat, Security Information and Event Management (SIEM), Security Orchestration Automation and Response (SOAR), and incident management tools or to custom remediation playbooks.
Below is the snapshot of features across AWS Control Tower, Cloud Custodian and Security Hub, as shown in the table, these solutions complement each other across the common compliance needs.
| SI No | AWS Control Tower | Cloud Custodian | Security Hub |
|---|---|---|---|
| 1 | Easy to implement or configure AWS Control Tower within few clicks | Light weight and flexible framework (Open source) which helps to deploy the cloud policies | Gives a comprehensive view of security alerts and security posture across AWS accounts |
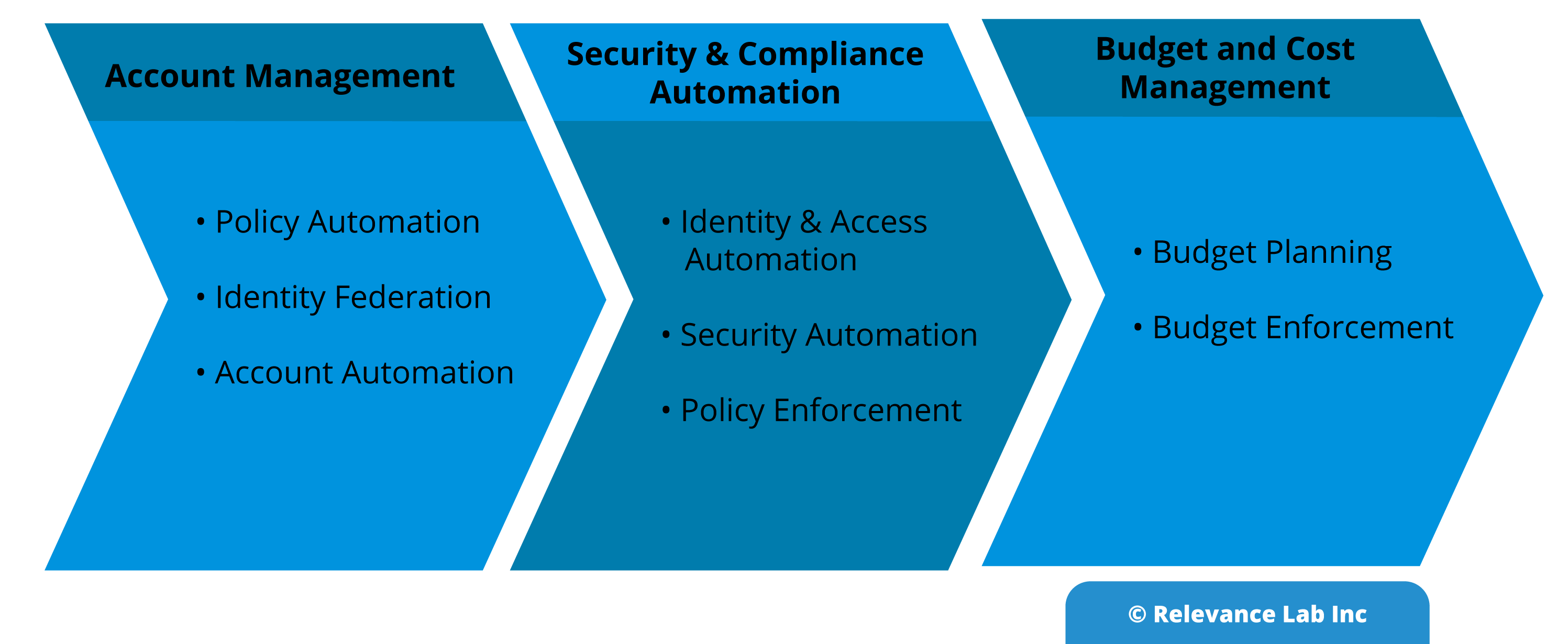
| 2 | It helps to achieve “Governance at Scale” – Account Management, Security, Compliance Automation, Budget and Cost Management | Helps to achieve Real-time Compliance and Cost Management | It’s a single place that aggregates, organizes, and prioritizes your security alerts, or findings, from multiple AWS services |
| 3 | Predefined Guardrails based on best practices – Establish / Enable Guardrails | We need to define the rules and Cloud Custodian will enforce them | Continuously monitors the account using automated security checks based on AWS best practices |
| 4 | Guardrails are enabled at Organization level | If an account has any specific requirement to either include or exclude certain policies, those exemptions can be handled | With a few clicks in the AWS Security Hub console, we can connect multiple AWS accounts and consolidate findings across those accounts |
| 5 | Automate Compliant Account Provisioning | Can be included in Account creation workflow to deploy the set of policies to every AWS account as part of the bootstrapping process | Automate continuous, account and resource-level configuration and security checks using industry standards and best practices |
| 6 | Separate Account for Centralized logging of all activities across accounts | Offers comprehensive logs whenever the policy is executed and can be stored to S3 bucket | Create and customize your own insights, tailored to your specific security and compliance needs |
| 7 | Separate Account for Audit. Designed to provide security and compliance teams read and write access to all accounts | Can be integrated with AWS Config, AWS Security Hub, AWS System Manager and AWS X-Ray Support | Diverse ecosystem of partner integrations |
| 8 | Single pane view dashboard to get visibility on all OU’S, accounts and guardrails | Needs Integration with Security Hub to view all the policies which have been implemented in regions / across accounts | Monitor your security posture and quickly identify security issues and trends across AWS accounts in Security Hub’s summary dashboard |
Relevance Lab Compliance as a Code Framework
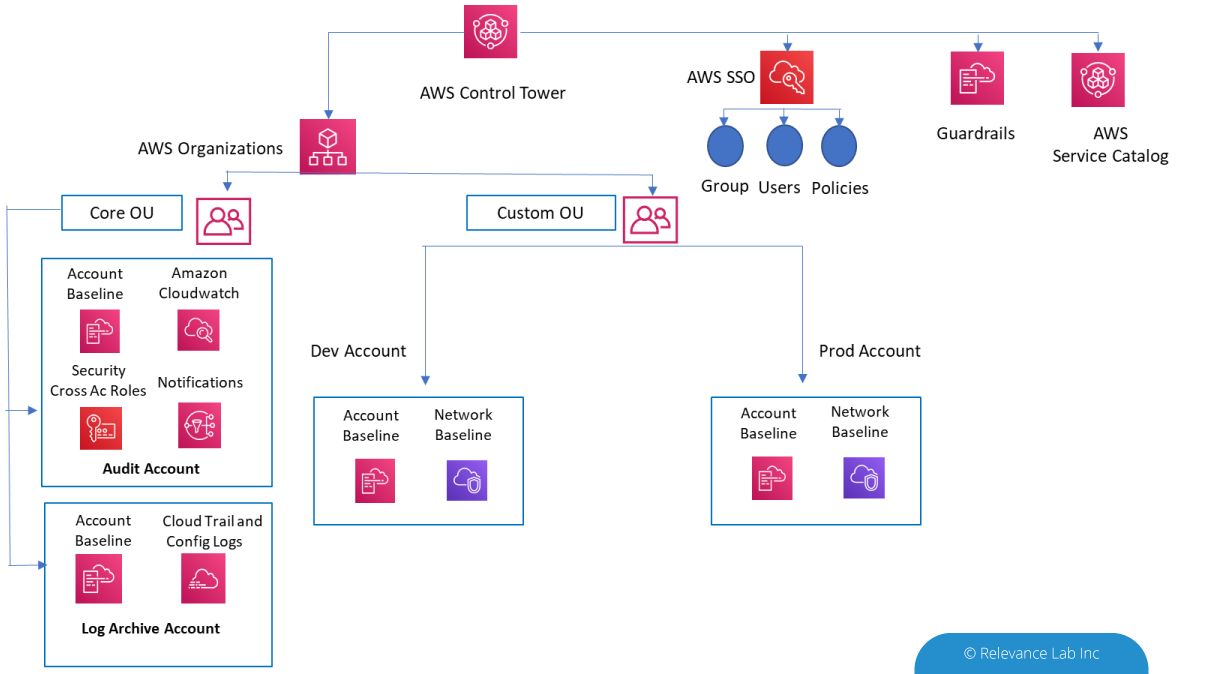
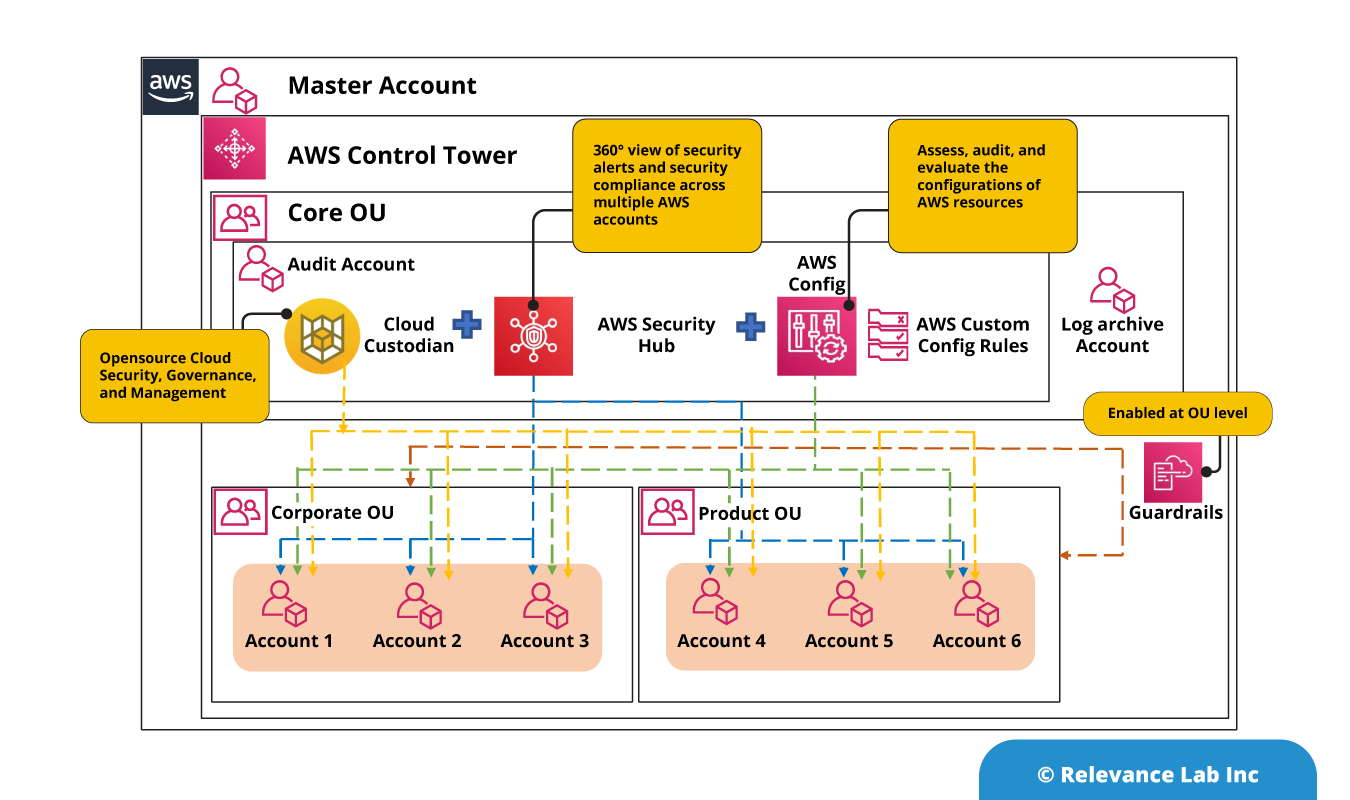
Relevance Lab’s Compliance as a Code framework is an integrated model between AWS Control Tower (CT), Cloud Custodian and AWS Security Hub. As shown below, CT helps organizations with pre-defined multi-account governance based on the best practices of AWS. The account provision is standardized across your hundreds and thousands of accounts within the organization. By enabling Config rules, you can bring in the additional compliance checks to manage your security, cost and account management. To implement events and action based policies, Cloud Custodian is implemented as a complementary solution to the AWS CT which helps to monitor, notify and take remediation actions based on the events. As these policies run in AWS Lambda, Cloud Custodian enforces Compliance-As-Code and auto-remediation, enabling organizations to simultaneously accelerate towards security and compliance. The real-time visibility into who made what changes from where, enables us to detect human errors and non-compliance. Also take suitable remediations based on this. This helps in operational efficiency and brings in cost optimization.
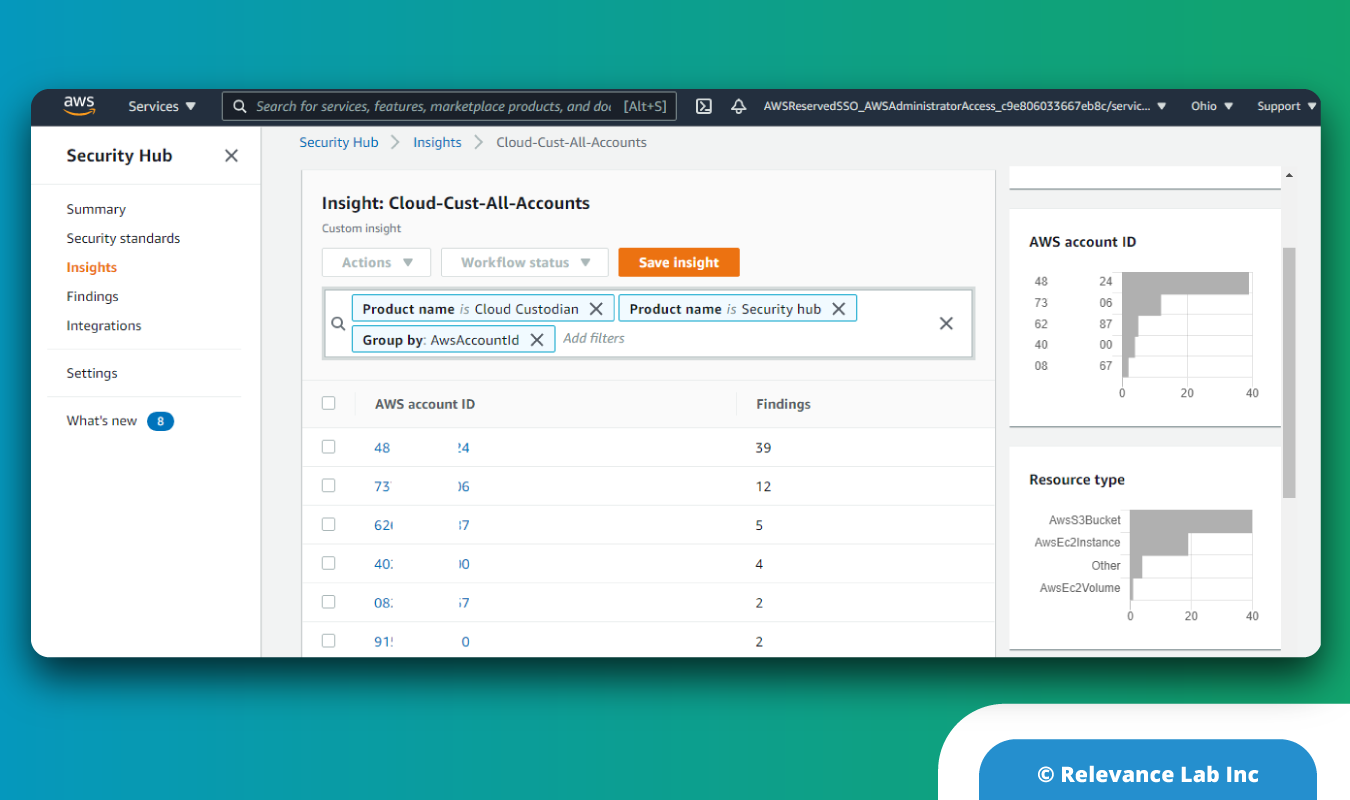
For eg: Custodian can identify all the non tagged EC2 instances or EBS volumes that are not mounted to an EC2 instance and notify the account admin that the same would be terminated in next 48 to 72 hours in case of no action. Having a Custom insight dashboard on Security Hub helps admin monitor the non-compliances and integrate it with an ITSM to create tickets and assign it to resolver groups. RL has implemented the Compliance as a Code for its own SaaS production platform called RLCatalyst Research Gateway, a custom cloud portal for researchers.
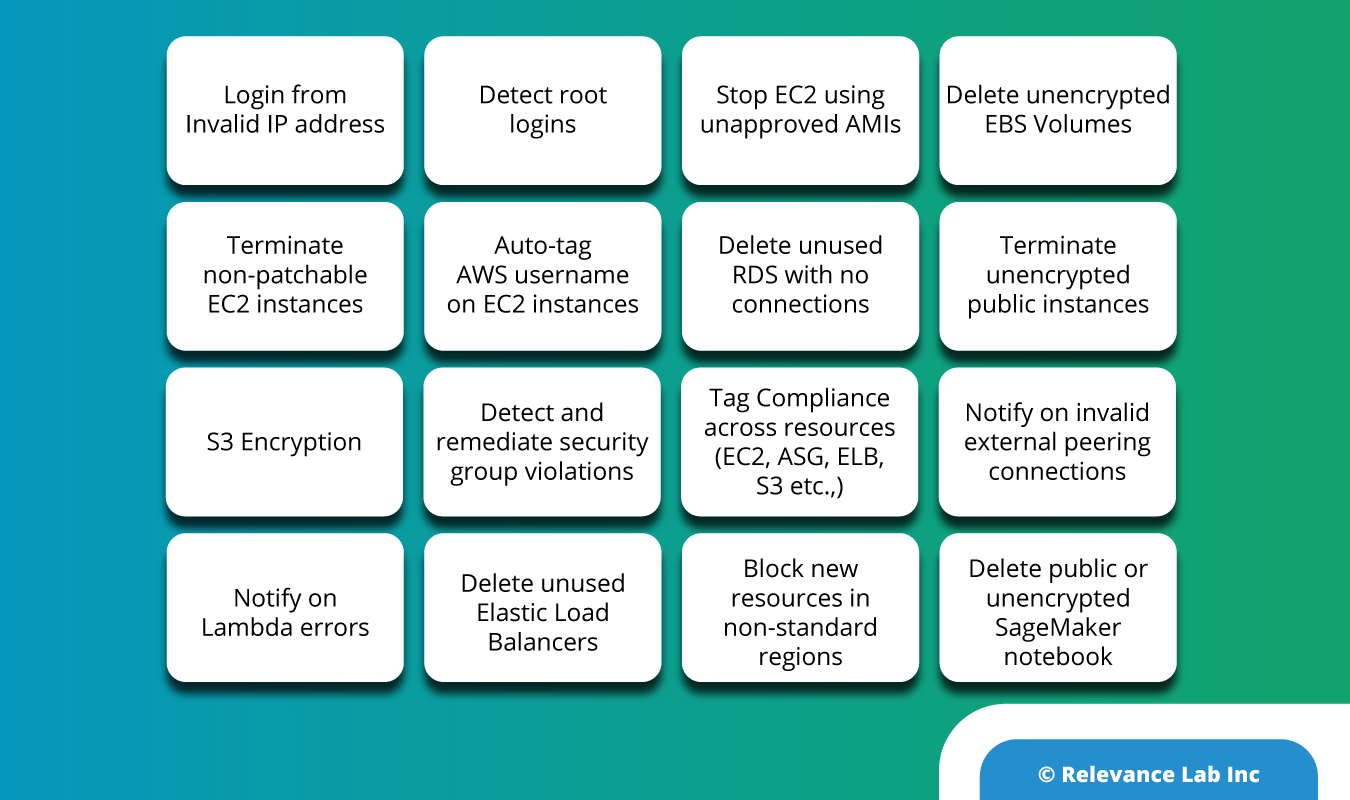
Common Use Cases
How to get started
Relevance Lab is a consulting partner of AWS and helps organizations achieve Compliance as a Code, using the best practices of AWS. While enterprises can try and build some of these solutions, it is a time consuming activity and error prone and needs a specialist partner. RL has helped 10+ enterprises on this need and has a reusable framework to meet the security and compliance needs. To start with Customers can enroll for a 10-10 program which gives an insight of their current cloud compliance. Based on an assessment, Relevance Lab will share the gap analysis report and help design the appropriate “to-be” model. Our Cloud governance professional services group also provides implementation and support services with agility and cost effectiveness.
For more details, please feel free to reach out to marketing@relevancelab.com